Research Article - Journal of Finance and Marketing (2018) Volume 2, Issue 3
Financial fraud and the effect of insider abuse in Nigerian banking sector
Udo E Samuel1, Ben E Udoh2, Abner I Prince2*, Ike R Nneka2, Ibekwe U John21Department of Banking, Enugu Campus, University of Nigeria, Nigeria
2Department of Management, Enugu Campus, University of Nigeria, Nigeria
- Corresponding Author:
- Abner I Prince
Department of Management, Enugu Campus
University of Nigeria, Nigeria
Tel: +2348069202051
Email: prince.abner.19910@unn.edu.ng
Accepted date: July 31, 2018
Citation: Samuel UE, Udoh BE, Prince AI, et al. Financial fraud and the effect of insider abuse in Nigerian banking sector. J Fin Mark. 2018;2(3):14-22.
DOI: 10.35841/finance-marketing.2.3.14-22
Visit for more related articles at Journal of Finance and MarketingAbstract
The fundamental objective of this study is to scrutinize the effect of insider abuse in the Nigerian banking sector along with its rudimental causes. The Classical Linear Regression Model (CLRM) was adopted along with secondary data extracted from the Nigeria deposit insurance corporations (NDIC) annual account report 2000-2016. The Ordinary Least Square technique signifies the prime technique of analysis as recommended by the ADF unit root test result. The ADF unit test revealed dataset stationarity at first order difference I(1). The R2 explains that 76.32% of the variation in the dependent variable is explained by the principal regressors. Total cases of fraud and amount involved were established to have a positive link with the total expected loss while, staff involvement, and total expected loss established negative and non-significant link. The study established that fraud in relation to insider abuse is not peculiarly Nigerian. The results bare that insider abuse are breed where there is weak and faulty internal control, lack of job security and reward for excellence. Recommendations are that financial institutions must review their internal control system, along with staff salary, the quality of staffs recruited and the audit system of the bank
Keywords
Fraud, Insider abuse, Total amount involved, Financial institution, Nigeria.
Introduction
The financial sector empirically and conventionally has been recognized as one of the fulcrum for growth and development of any economy. The financial sector in its conglomerate embraces financial (banking) and non-financial (non-banking) sectors in emerging and developed economies. The prime function of the banking sector embraces fund mobilization and allocation from the sufficient to the insufficient units herein referred to as financial intermediation. Fraud historically dates far back to the creation of mankind, as such its sprouts up straight from the human heart. In the contemporary era, fraud has assumed an endemic degree, with its negative effect resulting to, economic and financial crisis globally. Such is therefore, traceable to the Nigeria indigenous banks distress of the 1930s, 1940s, 1952, 1954, 1990s, and the 2008-2010 financial, and global economic crisis.
Consequently, fraud distraught operational activities of financial and non-financial businesses in developed and emerging economies [1]. Hence, The United States of America play host to her fair share of fraudulent undertakings resulting in huge financial loses according to evidence report of Wilhelm. Uchenna and Agbo [1] valued annually across various sectors of the economy; $67billion (Insurance), $150billion (Telecommunication), $1.2billion (Bank), $40billion (money laundered), $5.7billion (Internet) and $1billion (Credit card). Within the Nigerian context the Nigerian Deposit insurance corporations (NDIC) annual account report revealed that in 1998 about N 689.2million was lost to fraud, N2730.57million in 1999, N 2851.11million in 2000 and N11, 243.98million in 2001, N 2.9billion in 2007, N 17.5 billion in 2008, N 7.5 billion in 2009, N 4.071 billion in 2010, N 28 billion in 2011, N 25 billion in 2014 and N 18 billion in 2015 respectively [2].
The magnitudes of the losses incur and the operational effects on the financial institution translate to a significant peril to depositors and investors’ confidence in the operational activites of the industy. Hence, financial negligence in the banking industry has been established over the time as the breeding ground for fraud both within and outside the industry embracing institutional (insider abuse) and environmental factors. Zuraidah, Mohd Nor and Yusarina [3] holds the view, the fundamental intent of fraudsters is that of monetary gains which therefore placed the banking sector at the mercy of fraudulent individuals within and outside the system.
The American Federal Bureau of Investigation (FBI) pigeonholed financial fraud as a tier one tactical priority (U.S. Department of Justice Report, 2001) [3]. The decreasing cases of fraud and the increasing amount loss propels the Association of Certified Fraud Examiners (ACFE), report in 2014, establishing that the financial sector is more vulnerable to fraud owing to flaw in the internal control system even in the face of advanced technology employed to checkmate fraud within the external environment. Nevertheless, Zuraidah et al. [3] established factually that the pitiable state of management internal control system and the skimpy state of corporate governance breeds fraud and fraud is one of the prime quandaries in the industry. As such no depository is fraud immune in both developed and emerging economies. Based upon the documented indices, the study sort to scrutinize the foundational effect and causes of fraud in relation to insider abuse in the Nigerian financial sector.
Statement of Problem
Financial fraud globally dates far back to the creation of mankind and in the Nigerian financial world fraud dates far back to 1930s the era of industrial and commercial bank distress. The magnitude of unprincipled financial activities within the industry and outside propels the Transparency International corruption index report of 2018 ranking Nigeria as the 168th most corrupt nation in the world. In 2014, the CBN liquidated 83 microfinance banks squarely because of fraudulent activities and on February 17, 2015, hackers pulled off USD $80 billion from Bank Heist. The unrelenting cases of fraud and the increasing amount involved proportionally diminish depositors and investors’ confidence in the Nigerian financial system. The above therefore begs the question what are the fundamental factors responsible for insider abuse and if factors outsider the financial system equally drives fraudulent undertakings within the financial system? The prime objective of the study is to scrutinize the effect of financial fraud as it relates to insider abuse in the financial sector, with the specific the objectives to:
1. Ascertain the total amount involved in bank fraud in Nigeria.
2. Identified the categories of staff involved in bank fraud in Nigeria.
3. Ascertain the foundational factors responsible for bank fraud in Nigeria.
Review of Related Literature
Fraud
financial fraud globally has been recognized as one of the prime factors undermining the effectiveness, and efficiency of financial and non-financial institutions. The financial institution globally and constantly at the mercy of fraudsters via financial and technological manipulation owing to her tradeable commodities of cash and non-cash equivalents. The Federal Bureau of Investigation (FBI) [4], define fraud as falsified alteration and tracking down of financial transactions end to end under fabricated pretense. Eseoghene [5] acknowledged fraud to be premeditated exploit calculated towards unjustifiable gain at the detriment of naive individuals. Empirical researches identify fraud as a function of theft, assets treachery, and proceedings alternation for direct and indirect gains. Nevertheless, Enofe, Abilogun, Omoolorum and Elaiho [6] noted that, fraud emanate in the index of three fundamental essentials under the connotation “WOE” (Will, Opportunity, and Exit), with the sum of as a product of pressure, opportunity and rationalization the Donald Cressey's Fraud Triangle of 1950.
The Nigerian Economic and Financial Crime Commission (EFCC) Act of 2004 captures economic and financial crimes to fall within the armpit of:
“violent, criminal and forbidden undertakings in a fashion that infringes
prevailing statute… embracing money laundering, embezzlement, bribery,
looting and unprofessional conduct, oil bunkering, tax evasion, foreign
exchange abuse, intellectual theft, and open market abuse, etc (p. 29)
Varieties of Financial Fraud
Economic and finance researches pigeon-holed fraud in relation to its dimensions, nature, and forms. The above classification play host to Nwanze, Owolabi [7] categorizing fraud into, executive fraud and other fraud related undertakings. Owolabi [7] equally classified fraud into, executive, foreign exchange and domestic operations, money market and treasury, risk assets, information technology, financial control, clearing, fund transfer, teller operations and customer services related frauds.
Consequently, fraud in relation to perpetrators and environment are then segmented into two classifications;
1. Institutional (insider abuses): traceable to the internal financial environment.
2. Environmental (external factor): traceable to the external financial environment.
Institutional fraud according to Idowu and Adedokun [8] takes on:
1. Management fraud (top, middle and lower)
2. Employee fraud (staffs; skilled, unskilled and semiskilled)
Management fraud
Ajala, Amuda and Arulogun [9] identified management fraud as a function of records and account manipulation, stereotypically carried out by top, middle and lower level managers with the prime intent of direct or indirect benefits. The victims of such frauds are investors and depositors and the financial statement act as the prime instrument for perpetration of such fraudulent activities.
Employee fraud
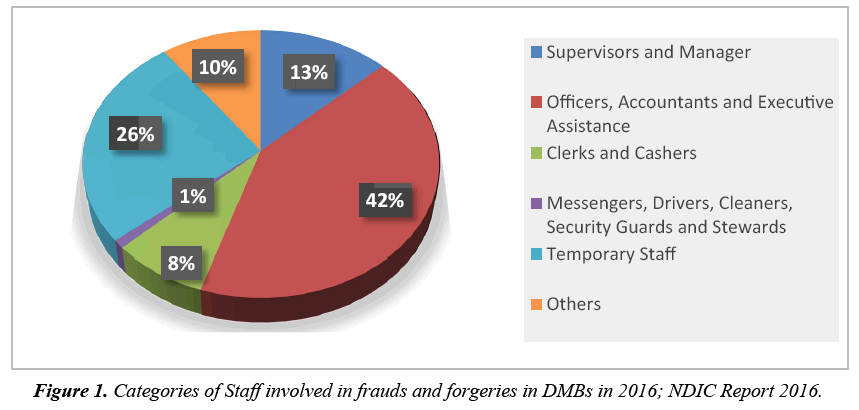
Employee fraud is equally referred to as non-management fraud, perpetrated by the employees embracing skilled, semi-skilled and un-skilled staffs. The prime instrument of perpetration takes on document falsification, violation of staff code of conducts and employer’s policies, along with financial embezzlement. As such Awe [10] established the following as employee fraud where fictitious payment of supplies and wages falsification (payroll fraud) takes place. Table 1 shows the highest fraud cases from 2014-2016 according to the DMBs report and Figure 1 depicts the staff involvement in fraudulent activities.
| GROUP | 2014 | 2015 | 2016 | |||
|---|---|---|---|---|---|---|
| Amount Involved (N’M) | % Share |
Amount Involved (N’M) | % Share |
Amount Involved (N’M) |
% Share |
|
| Top 10 DMBs | 21,904.45 | 85.54 | 16,261.64 | 90.23 | 7,625.90 | 87.83 |
| Total for all DMBs | 25,608.06 | 100 | 18,022.49 | 100 | 8,682.66 | 100 |
Table 1: DMBs with the highest fraud cases from 2014 to 2016.
Insider abuse and dealings
Fraud in relation to insider abuses are perpetrated owing to the fragile operational and internal control systems of the financial institutions. As such Zuraidah et al. [3] are of the view, fraudulent activities are calculated act by an individual or a group of individuals among the management, staff or third parties. The OCPS Internal Audit Department report acknowledged fraud as detrimental act on the bank with direct and indirect benefits enjoyed by perpetrators, which undermines the efficiency of banks along with its fundamental objective of financial intermediation. According to KPMG (2013) reports on financial system fraud 85% of the respondents holds the view, fraud is progressively industry associated with the banking sector primarily becoming risktaking industry. Frauds especially in the financial institution are very expansive. It could cover from employee fraud to customer fraud; from institutional fraud to individual fraud; and from accounting fraud to transactional fraud. Table 2 shows different categories staff involved in frauds from 2014-2016.
| Status | 2014 | 2015 | 2016 | |||
|---|---|---|---|---|---|---|
| Number | % | Number | % | Number | % | |
| Supervisors & Managers | 58 | 12.47 | 62 | 14.59 | 31 | 13.42 |
| Officers, Accountants & Executive Assistants | 176 | 37.85 | 119 | 28 | 98 | 42.42 |
| Clerks & Cashiers | 78 | 16.77 | 69 | 16.24 | 18 | 7.79 |
| Messengers, Drivers, Cleaners, Security Guards & Stewards | 2 | 0.43 | 11 | 2.59 | 1 | 0.43 |
| Temporary Staff | 126 | 27.1 | 164 | 38.59 | 59 | 25.54 |
| Others | 25 | 5.38 | - | - | 24 | 10.39 |
| Total | 465 | 100 | 425 | 100 | 231 | 100 |
Table 2: Categories of staff involved in frauds and forgeries from 2014 to 2016.
Effect of insider abuse: The major effects of insider abuse in financial environment are bank based capital deterioration, loss of public confident and financial and economic distress.
Irrespective of type and the nature of the frauds, Table 3 depicts information related to the frequency of the fraud with actual losses sustained by DMBs.
| 2015 | 2016 | |||
|---|---|---|---|---|
| Nature of fraud |
Frequency | Actual loss sustained(N’b) |
Frequency | Actual loss sustained(N’b) |
| ATM/Card-Related Fraud |
8039 | 0.504 | 11244 | 0.476 |
| Web-Based (Internet Banking) Fraud |
1471 | 0.857 | 3689 | 0.582 |
| Fraudulent Transfers/ Withdrawal of Deposits |
1396 | 0.562 | 836 | 0.626 |
| Suppression of Customer Deposits |
602 | 0.218 | 357 | 0.224 |
| Fraudulent Conversion Of Cheques |
71 | 0.049 | 48 | 0.002 |
| Presentation of Stolen Cheques |
132 | 0.054 | 17 | 0.014 |
| Presentation of Forged Cheques |
69 | 0.067 | 59 | 0.021 |
| Outright Theft by Staff(cash defalcation ) |
213 | 0.146 | 182 | 0.179 |
| Unauthorized Credits | 143 | 0.587 | 172 | 0.198 |
| Outright Theft by Outsiders/Customers |
33 | 0.021 | 24 | 0.021 |
| Foreign Currencies Theft |
18 | 0.033 | 26 | 0.033 |
| Diversion of Bank Charges (Commissions & Fees) |
92 | 0.075 | 83 | 0.034 |
| Lodgement of stolen Warrants |
14 | 0.034 | ||
| Total | 12,279 | 3,173 | 16,751 | 2,446 |
Table 3: Type and frequency of frauds with actual losses sustained by deposit money banks (DMBs) in 2015-2016.
Other forms of financial frauds
1. Advance Fee Fraud (419) and Forged cheque, Cheque Kitting and cheque cloning
2. Account Opening Fraud and Counterfeit Financial Securities
3. Money Transfer Fraud, Letter of Credit Fraud, loan fraud, and Clearing Fraud
4. Duplicating or skimming card data, copying magnetic stripe information off a card for duplication [2].
Theoretical Framework
Donald cressy's fraud triangle of 1950
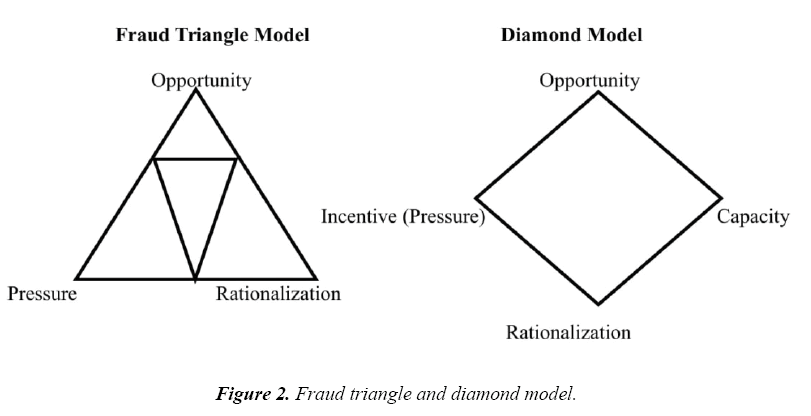
The fraud triangle model was propounded by Donald Cressy an American criminologist in 1950 to ascertain the prime and core ingredients propelling fraudulent activities in financial and non-financial institutions globally as it relates to internal and external factors. The prime ingredients as instituted by Donald Cressy correlating fraud embrace opportunity, pressure, and rationalization. The triangle fraud model is however accredited to be an end product of the Sutherland’s Criminal Research Study Report herein referred to as the White Collar Crime (management and staff fraud). Sutherland, established white-collar crime as fraudulent undertakings embark upon by decent and high ranking individuals at the managerial level, board of directors and senior staffs at the detriment of the employer, customers and third party. As such empirical arguments emanating from the Sutherland’s Criminal Research Study Report noted that white collar fraudsters are brainy, opportunists, and educated individuals. Berney [11] acknowledged that, about 78% of financial frauds are committed squarely by insiders where opportunity, pressure, and rationalization exist. Figure 2 depicts the triangle and diamond model.
Wolf and Hermanson [12] argued that about 80% of fraudulent undertakings in the financial and non-financial institutions are accredited to individual capacity. He explained that capacity propels fraud more than opportunity since capacity embraces technical know-how and up-to-date knowledge on the operational activities of the target institution specifically the financial institution.
Ajzen and fishbein fraud reasoned action of 1975
The Fraud Reasoned Action Model of 1975 as theorized by Ajzen and Fishbein is accredited to be a product of social psychology as it relates to belief, attitude, norms, and morals. The 1975 model, noted that belief, attitude, norms, and morals are the prime propellers of fraudulent activities. As such Ajzen and Fishbein in their argument states that, behavior is a function of attitude, action is an end product of norms and morals, which therefore holds the fact that folks with the erroneous belief, attitude, norms and morals are likely to embark on fraudulent activities, at the detriment of their employers, third parties and against government agencies. The Differential Opportunity model of Comer 1986 agrees with the fraud reasoned action model of 1975 [7]. Rex and Subramaniam [13] noted that, fraud and other related unethical undertaking transpires where individuals lack ethical logic which therefore agrees with Comer 1986 Concealment Model. Nevertheless, Rex and Subramaniam [13] equally established that greed (gluttony) propels fraudulent activities.
Empirical Frame Work
Kanu and Okorafor [14] reviewed the nature, extent and economic impact of financial conditions in financial institutions in Nigeria, especially in deposit money banks by means of descriptive and inference statistics. Research result bears the presence of a positive significant correlation flanked by bank deposit and fraudulent activities in the banking industry. Sang [15] empirically studied the prime contributing factors to fraud and its resistor techniques in deposit money banks in Kenya.
By means of descriptive research design and inferential statistics embracing the questionnaires adoption for data. Research results bear that the internal control inefficiency is an end product of non-adherence control trait and time insufficient inconsonant to various periodic tests. Recommendation is that all-inclusive technique adopted to checkmate fraud must enforce and in compliance to fraud easing methods. Ajala, Amuda and Arulogun [9] scrutinize the impact of internal control in relation to checkmating financial deposit money banks in Nigeria. An analyzed by means of product moment correlation coefficient and regression analysis, with data extracted from audited and published financial statements of selected deposit money banks in Nigeria. Findings show that effective and efficient internal control system significantly foils and restrain financial frauds in DMBs banks. In conclusion, they hold the view that, corrupt corporate governance is solely responsible for ill-mannered internal control system paving way for fraud to thrive. Zuraidah, Mohd Nor and Yusarina [3] probed fraud patterns in deposit money banks along with its precautionary measure in Malaysia. The study areas center on branch managers and assistants’ managers in relation to mortgage and hire purchase loans. Findings show that fraud perpetrators understand the procedure involved in loans procurement and duly takes advantage and capitalize on it penetrate to commit fraud. They concluded that it is impossible to achieve zero fraud risk as the respective staff’s roles could be more visible in combating fraud. Olaoye, Dada, and Adebayo [16] examine frauds in deposit money banks in relation to Nigeria’s experience. The prime focus is to gauge the nature, causes, effects, detection and prevention measure in Nigeria. The study adopted descriptive technique by means of primary data via questionnaires. They recommended that DMBs ought to embrace the following as techniques to checkmate fraud; efficient and effective internal control, satisfactory remuneration and reward for excellence while unremitting and sporadic downscaling of staffs ought to be discouraged.
Knowledge Gap
The review of related literature indicates that various studies on financial fraud concentrated on the external factors propelling fraud along with its impact on the financial institution, while ignoring the foundational causes of fraud embracing internal (institutional) as it relates to insider abuse. However, this study is unique as it fills the knowledge gap by way of investigating the effect of insider abuse as it relates to financial fraud in Nigeria. Data employ in the study run from 2000-2016, coving recent and past fraudulent activities in the financial sector as published by the Nigerian Deposit Insurance Corporation (NDIC) annual report [2]. The model stability diagnostic test of cumulative sum of squares graph (CUSUM) was employ to ensure the research model is stable and it solves the problem of the study along with an array of tests.
Methodology
Ex-post facto research design technique is adopted as an ideal technique for the study and in steering analysis in business and social sciences. Ex-post facto design embraces fact with previous deeds as such the proxies for the variables of interest are not prone to controls or doctored by the researcher since such information’s are in public sphere and are certainly verifiable.
Sources and nature of data
The data for the study was sourced and exacted from the Nigerian Deposit Insurance Corporation (NDIC) annual report (2000-2016) as published [2]. The justification for the based the year 2000 play host to the new millennium, renewed technique and advanced technology employed along with policies to checkmate insider abuse in the financial institutions.
Technique of analysis
The study adopted descriptive statistics and OLS technique. Augmented Dickey-Fuller (ADF) test for unit root test along with a collection of diagnostic tests carried out on the regression model to ensure the strategic customs underlying the Classical Linear Regression Model (CLRM) are not defiled. The diagnostic tests carried include; White’s Heteroskedasticity Test, Ramsey Regression Error Specification Test (RESET), Breusch Godfrey Serial Correlation Tests, Durbin Watson Test and the Cumulative Sum of Squares (CUSUM) recursive estimates tests/graph.
Model specification
The study adopts the Classical Linear Regression Model of AR Abdul Rasheed, Isiaka Sulu Babaita, Muhammed Abubakar Yinusa [17]. The model was modified to capture Insider Abuse, the essential variables are fitted in on the CLRM and log-transformed to ensure linearity and it appears thus:
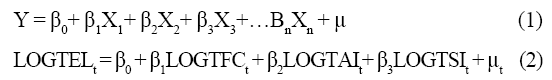
The research data for the study were capture as published by the Nigerian Deposit Insurance Corporation (NDIC) annual report (2000-2016) [2];
Where:
TFC = Total Number of Fraud Cases,
TAI = Total Amount Involved,
TEC = Total Expected Loss,
TSI = Staff Involvement,
μ = error term,
Β1, β2, = coefficients of the parameter estimate or the slopes,
β0 = Intercept of the regression equation
Apriori expectation: β1, β2 > 0 and β3 <0
Presentation and Analyses of Data
Data description
Basic descriptive statistical values of variables which are under study given in Table 4 display the rudimentary aggregative averages of mean and median. Standard deviation measures the degree of spread and variations, whereas, kurtosis measures the degree of peakedness while skewness measures the degree of or departure from symmetry. Jarque-Bera Statistics measures normality confirming all observations are platykurtic with their kurtosis less than 2 and the p-values of the JB Statistics are greater than 5%.
| LOGTEC | LOGTAI | LOGTFC | LOGTSI | |
|---|---|---|---|---|
| Mean | 7.959518 | 9.575088 | 7.547954 | 5.788563 |
| Median | 8.064636 | 9.466532 | 7.347944 | 5.948035 |
| Maximum | 8.843471 | 10.88787 | 9.726213 | 6.525030 |
| Minimum | 6.753438 | 7.955425 | 5.998937 | 4.442651 |
| Std. Dev. | 0.671510 | 0.735083 | 0.933777 | 0.596125 |
| Skewness | -0.574369 | -0.287844 | 0.831866 | -0.99923 |
| Kurtosis | 2.173058 | 2.959815 | 3.393129 | 3.108093 |
| Jarque-Bera | 1.419097 | 0.235897 | 2.070141 | 2.837250 |
| Probability | 0.491866 | 0.888742 | 0.355201 | 0.242047 |
| Sum | 135.3118 | 162.7765 | 128.3152 | 98.40557 |
| Sum Sq. Dev. | 7.214813 | 8.645552 | 13.95103 | 5.685846 |
| Observations | 17 | 17 | 17 | 17 |
Table 4: Description of Variables under Study.
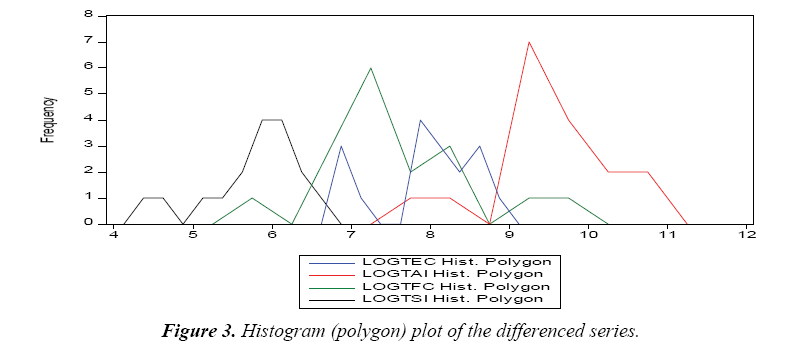
Figure 3 above displays a histogram (Polygon) Plot where the total number of fraud cases (TFC) has the highest peak with the highest values of observations. The plot also shows that the variables fall within the range. However other variables of the study show moderate values which revealed the existence of possible linear association.
Tests for unit root
A group unit root test was conducted for the variables by means of ADF. The results indicate that the series are cointegrated at I(1) first order difference.
Table 5 above, embraces indicators of individual unit root and common unit root tests with the p values (0.000) less than 5%. The results propel the rejection of the null and acceptance of alternative hypotheses.
| Group unit root test: Summary | ||||
| Series: LOGTEC, LOGTAI, LOGTFC, LOGTSI | ||||
| Date: 03/30/18 Time: 14:23 | ||||
| Sample: 2000 2016 | ||||
| Exogenous variables: Individual effects | ||||
| Automatic selection of maximum lags | ||||
| Automatic lag length selection based on SIC: 0 to 2 | ||||
| Newey-West automatic bandwidth selection and Bartlett kernel | ||||
| Method | Statistic | Probs.** | Cross-sections | Observation |
| Null: Unit root (assumes common unit root process) | ||||
| Levin, Lin & Chu t* | -9.35535 | 0.0000 | 4 | 56 |
| Null: Unit root (assumes individual unit root process) | ||||
| Im, Pesaran and Shin W-stat | -8.36929 | 0.0000 | 4 | 56 |
| ADF-Fisher Chi-square | 57.1950 | 0.0000 | 4 | 56 |
| PP-Fisher Chi-square | 52.5766 | 0.0000 | 4 | 60 |
**Probabilities for Fisher tests are computed using an asymptotic Chi-Square distribution. All other tests assume asymptotic normality
Table 5: Unit Group Root Test.
The estimated results in Table 6 above display the affiliation flanked by financial fraud in relation to insider abuse in Nigeria contained by the model. Positive affiliation exists between ΔTFC, ΔTAI, and ΔTEC. The above are therefore consistent with apriori expectation of the study. However, a negative and non-significant bond exists between ΔTSI and ΔTFC. This is therefore a departure from the expected signs and directions. The R2 value of 76.32% explains the variations in TEC within the context of the model; such is equally explained by the regressors. The Adjusted R2 value of 70.86%, confirms the model goodness of fit. The F-test value of 13.97230 and the p-value of (0.0000*) confirms that the regression model is statistically significant at 5%. The DW statistics of 1.37, by the rule of thumb, rules out the suspicion of AR (1) autocorrelation and substantiates data stability. The Breusch Godfrey LM serial correlation was conducted to confirm for autocorrelation which is shown in Table 7.
| Dependent Variable: LOGTEC | |||||
| Included observations: 17 | |||||
| Option in OLS: White Heteroskedasticity Consistent Errors and Covariance | |||||
| Variable | Expectation | Coefficient | Std. Error | t-Statistic | Prob. |
| LOGTAI | + | 0.391165 | 0.139549 | 2.803078 | 0.0149 |
| LOGTFC | + | 0.149917 | 0.111195 | 1.348231 | 0.2006 |
| LOGTSI | - | 0.579906 | 0.162513 | 3.568365 | 0.0034 |
| Other OLS Estimates | |||||
| R2 = 76.32% | |||||
| Adjusted R2 = 70.86% | |||||
| F-Statistic = 13.97320 | |||||
| Prob(F-Statistic) 0.0000 | |||||
| (Dw Stat 1.37) | |||||
The Probability values * means significance at 5% level
Table 6: Regression Results.
| Breusch-Godfrey Serial Correlation LM Test | |||
|---|---|---|---|
| F-statistic | 0.500138 | Prob. F(2,11) | 0.6196 |
| Obs* R-squared | 1.417026 | Prob. Chi-Square(2) | 0.4924 |
Table 7: The Breusch Godfrey lm serial correlation test.
The BG LM serial correlation test result takes in a lag of 2 by the rule of thumb represents one-third of the number of observations indicates that the p-values of the F and Chisquare tests are all greater than 5%. Therefore, we accept the null hypothesis of no autocorrelation. This confirms the DW results and absolves the regression results of all forms of spuriousness.
The White Test for heteroscedasticity result display in the Table 8 above rejects the null hypothesis of homoscedasticity. That is, therefore, a clear violation of the prime cardinal assumptions of the Linear Regression Model. To remedy such problem, the regression result, the white heteroscedasticityconsistent standard errors and covariance gave us a more robust standard error and t-estimates as reported above.
| Heteroskedasticity Test: White | |||
|---|---|---|---|
| F-statistic | 0.244981 | Prob. F(9,7) | 0.9728 |
| Obs*R-squared | 4.072004 | Prob. Chi-Square(9) | 0.9066 |
| Scaled explained SS | 2.326341 | Prob. Chi-Square(9) | 0.9852 |
Table 8: Test for heteroskedasticity.
Table 9 above, displays the Trace statistic, Maximal Eigenvalue Statistic and Probability results which indicates that the presence of (1) co-integrating equation at 5% significance, which implies that total expected loss is cointegrated with insider abuse. Thus, the results suggest the existence of a stable long-run relationship between financial fraud and insider abuse.
| Hypothesized No. of CE(s) | Eigenvalue | Trace Statistic | 0.05 Critical Value | Prob.** |
|---|---|---|---|---|
| None * | 0.964317 | 72.13615 | 47.85613 | 0.0001 |
| At most 1 | 0.643922 | 22.13993 | 29.79707 | 0.2908 |
| At most 2 | 0.303425 | 6.650850 | 15.49471 | 0.6186 |
| At most 3 | 0.078553 | 1.227154 | 3.841466 | 0.2680 |
Trace test indicates 1 co-integrating eqn (s) at the 0.05 level
*denotes rejection of the hypothesis at the 0.05 level
**MacKinnon-Haug-Michelis (1999) p-values
Table 9: Co-integrating test result between financial fraud and insider abuse variables.
Table 10 above shows the Pairwise Granger Causality results which ultimately propose that there is a bi-directional relationship between financial fraud and insider abuse in Nigeria.
| Pairwise Granger Causality Tests | |||
| Date: 03/30/18 Time: 14:17 | |||
| Sample: 2000 2016 | |||
| Lags: 2 | |||
| Null Hypothesis | Observations | F-Statistic | Prob. |
| LOGTAI does not Granger Cause LOGTEC | 15 | 0.09428 | 0.9108 |
| LOGTEC does not Granger Cause LOGTAI | 0.78849 | 0.4809 | |
| LOGTFC does not Granger Cause LOGTEC | 15 | 0.08335 | 0.9207 |
| LOGTEC does not Granger Cause LOGTFC | 0.21281 | 0.8119 | |
| LOGTSI does not Granger Cause LOGTEC | 15 | 2.22972 | 0.1582 |
| LOGTEC does not Granger Cause LOGTSI | 1.27720 | 0.3206 | |
| LOGTFC does not Granger Cause LOGTAI | 15 | 0.50473 | 0.6183 |
| LOGTAI does not Granger Cause LOGTFC | 1.11506 | 0.3655 | |
| LOGTSI does not Granger Cause LOGTAI | 15 | 0.22678 | 0.8011 |
| LOGTAI does not Granger Cause LOGTSI | 0.59486 | 0.57 | |
| LOGTSI does not Granger Cause LOGTFC | 15 | 1.06524 | 0.3807 |
| LOGTFC does not Granger Cause LOGTSI | 0.83449 | 0.4622 | |
Table 10: Pairwise granger causality tests.
Test for model stability
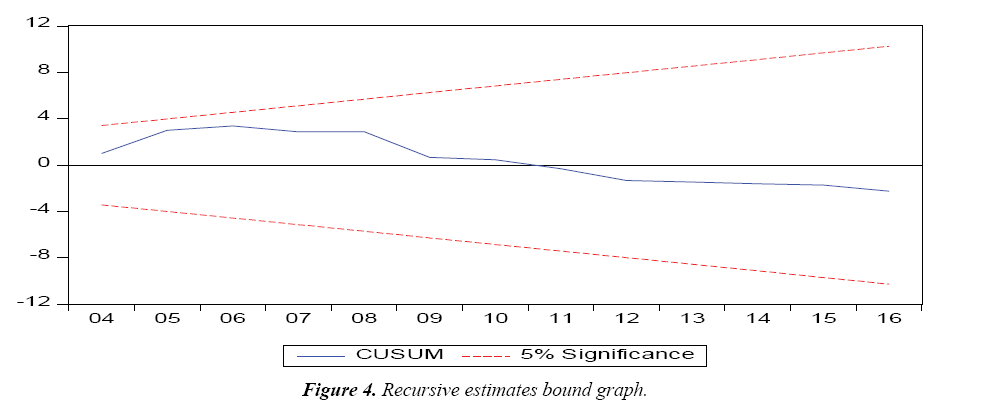
To confirm the stability of the model and the nonexistence of wrong functional form and model specification error, Ramsey RESET (Regression Specification Error Test) and the Recursive Estimates Bound Graph were adopted. The recursive graph depicted in Figure 4 indicates the red lines of the upper and lower bounds and the blue line indicating the model. This indicates that the model is blue and within bounds. The Ramsey RESET test as shown in Table 11 below, conducted on a lag of 1 show that there is no model specification error. Indicating that irrelevant variables were not included and essential variables were not omitted.
| Ramsey RESET Test | |||
|---|---|---|---|
| Equation: UNTITLED | |||
| Specification: LOGTEC LOGTAI LOGTFC LOGTSI C | |||
| Omitted Variables: Squares of fitted values | |||
| Value | Df | Probability | |
| t-statistic | 1.497108 | 12 | 0.1602 |
| F-statistic | 2.241332 | (1, 12) | 0.1602 |
| Likelihood ratio | 2.911110 | 1 | 0.0880 |
Table 11: Ramsey reset tests results.
Recommendation and Conclusion
The study analyses the effect of financial fraud with emphasis on Insider Abuses in the Nigerian banking sector using a dataset covering a 17 year period. The OLS technique denotes the prime technique of valuation pooled with variety of other universal/customary and diagnostic tests. The prime objective of the study is to scrutinize the fundamental causes of insider abuse even in the face of straight regulations and advance technology employed in the financial sector.
The R2 76.32% explains the variations in TEC within the context of the model such is therefore explained by the regressors. The Adjusted R2 of 70.86% shows that the model has a goodness of fit. The research findings and results display the existence of a positive affiliation between ΔTFC, ΔTAI, and ΔTEC, along with a negative and non-significant bond between ΔTSI and ΔTFC. The research findings are therefore consistent with the fraud theory which states that, increase in the number of fraud cases translate to increase in the amount involved Ceteris paribus.
There is, therefore, a strong recommendation and advocacy for an all-inclusive financial institution's internal control system review, staff recruitment process review, and audit reports review. Consequently, job security and reward for excellent must be re-established to encourage hard work and commitment to work, staff salary scale must be review in line with the current economic and financial strength of the national economy. Insider abuses, its control and elimination are the sole responsibility of management.
References
- Uchenna C, Agbo JC. Impact of Fraud and Fraudulent Practices on the Performance of Banks in Nigeria. British J Arts Social Sci. 2013;15(1):12.
- NDIC. Nigeria Deposit Insurance Corporation Annual Reports and Statement of Accounts for various years. 2000-2016.
- Zuraidah MS, Ramelib MNR, Isab YM. Fraud Schemes in the Banking Institutions: Prevention Measures to Avoid Severe Financial Loss. 7th International Conference on Financial Criminology, Wadham College, Oxford, United Kingdom, 2015.
- Federal Bureau of Investigation [FBI] Uniform crime reports. New York: U.S. Government Printing Office. 1984.
- Eseoghene JI, Bank Frauds in Nigeria: Underlying Causes, Effects, and Possible Remedies. African J Account Econ Fin Banking Res. 2010;6(6).
- Enofe AO, Abilogun TO, Omoolorum AJ, et al. Bank Fraud and Preventive Measures in Nigeria: An Empirical Review. Inter J Academic Res Business Social Sci. 2017;7(7): 42.
- Owolabi SA. Fraud and Fraudulent Practices in Nigerian Banking Industry. African Res Review. 2010;4(3b): 240-256.
- Idowu A, Adedokun TO, Internal Control System on Fraud Detection: Nigeria Experience. J Account Fin. 2013;13(5): 144.
- Ajala OA, Amuda T, Arulogun L, Evaluating internal control system as a preventive measure of fraud in the Nigerian banking sector. Inter J Manage Sci Business Res.2013;2(9): 15-22.
- Awe OI, The Theory and Practice of Auditing. Adeyemo publishing house, Akure, Nigeria, 2005.
- Berney L. “For online merchants, fraud prevention can be a balancing act”. Cards and Payments. 2008;21(2): 22-7.
- Wolf DT, Hermanson DR, The fraud diamond: considering the four elements of fraud. The Certified Public Acc J. 2004.
- Rex K, Subramaniam N, Quality of internal control procedures: Antecedents and moderating effect on organizational justice and employee fraud. Managerial Auditing J. 2008;23(2): 104-124.
- Kanu SI, Okorafor EO, The nature, extent and economic impact of fraud on bank deposits in Nigeria. Interdisciplinary J Contemporary Res Bus. 2013;4(9): 253-265.
- Sang MJ. Determinants of fraud control measures in commercial banks: A survey of selected commercial banks in Nakuru town, Kenya. Intern J Sci Res. 2012;3(10): 2178-2183.
- Olaoye CO, Dada RA. Adebayo AI, Analysis of Frauds in Banks: Nigeria’s Experience. Intern J Innovative Res Dev. 2014;(3)1.
- Abdul Rasheed AR, Babaita IS, Yinusa AM.Fraud and Its Implications for Bank Performance in NigeriaIntern J Asian Social Sci. 2012;2(4): 382-387.