Research Article - Biomedical Research (2018) Computational Life Sciences and Smarter Technological Advancement: Edition: II
Secured therapeutic applications for drug repositioning on the cloud computing
1Department of Computer Science and Engineering, Anna University, BIT Campus, Tiruchirappalli, Tamil Nadu, India
2Department of Mathematics, Anna University, BIT Campus, Tiruchirappalli, Tamil Nadu, India
- *Corresponding Author:
- M Padma
Department of Computer Science and Engineering
Anna University, BIT Campus
Tamil Nadu, India
Accepted on February 08, 2017
DOI: 10.4066/biomedicalresearch.29-17-255
Visit for more related articles at Biomedical ResearchAbstract
Computing is virtually invading all domains of businesses and the Pharmaceutical Industry is in fact the latest one to join this elite club that utilizes the cloud phenomenon to improve productivity and efficiency of pharmaceutical processes. From the existing drug, discovering a new drug with the help of cloud computing makes the production of drug as cost effective and minimize time to develop. Hence here proposed a methodology using effective resource utilization and fuzzy logic for the pharma industry to rely on modern cloud based technologies to effectively perform the drug repositioning. Complex events that involve intensive computing processes can be done at ease thereby increasing the scope of repositioning the existing drugs in a fast manner. However security of such systems needs to be improved and the existing methodologies involve a considerable loss in execution time and efficiency. This paper explores one such area where the security of cloud can be improved and customized according to the pharma industry with a relatively improved performance and efficiency.
Keywords
Drug repositioning, Drug repurposing, Fuzzy selection mechanism, Resource Management, Cloud storage, cloud security.
Introduction
To fight against diseases, conventional drug discovery methods involved hundreds of household scientists who spent huge time to discover a drug for therapeutic purpose. In modern world number of new technologies enable the drug discovery as the kernel of upcoming pharmacopoeias. Instead of developing a new drug from the scratch, it is identified that repositioning of existing drug compounds maximizes the effective utilization of resources available. The transformation from conventional to innovative methods reduces in invention time and rise in productivity. Applying cloud computing in drug discovery avoids the maintenance cost, reduces capital investment and can use enormous amount of resources (hardware, software, storage etc.) needed for the computation. The online drug information coupled with drug repositioning methods and processed in the cloud resources that enable fast computation, resource management and minimized time. The unsecured drug databases stored in cloud might be attacked by attackers. Employing privacy protecting encryption standards to drug databases eliminates such attacks.
Why Cloud Computing in Drug Repositioning
Cloud computing is a distributed computing model it provides computational specialty and resources depends on the request. The cloud computing information technology services gives new vision for a new type of surface that provides information and services [1,2]. Cloud computing is an effective technology to perform massive-scale and highly complex computing. It cuts the need to maintain expensive computing hardware, dedicated space, and software. Massive growth in the scale of data or big data generated through cloud computing has been observed. It is a large scale distributed paradigms which provides storages, platforms and services on-demand to external customers over internet. By using this technology storing drug based standard databases in cloud storage can perform repositioning drugs becomes easier and economic. In this paper, proposed a novel approach to improve the computational efficiency and time required to process the drug repositioning by this cloud computing resources. Hence every research unit involved produces large amounts of data to be captured and analyzed from multiple experiments consecutively, in need of effective integration of data and scientific knowledge from many disparate sources (sites) is very crucial to make valid scientific conclusions through multiple iterations in order to make it a success. By means of introducing cloud computing the data stored in cloud storage can help to increase the process of repositioning much faster and cost effective. This can achieved by collecting related databases which is large in size, into cloud storage and perform the repositioning strategies. This is implemented with the help of VMware.
Cloud Drug Repositioning
Several trends are opening up the era of Cloud Computing, which is an Internet-based development and use of computer technology. On demand basis the cloud resources have been utilized for the repurposing of the drugs by the researchers. From the beginning of the evolution of Drug repositioning the hope for finding new drug is increased [3]. Developing such a drug repositioning service gives rises to challenges including highly concurrent and scalable drug record retrieval, data analysis, as well as privacy protection. In this paper, we propose a cloud-based framework for implementing a drug repositioning approach to address the above challenges.
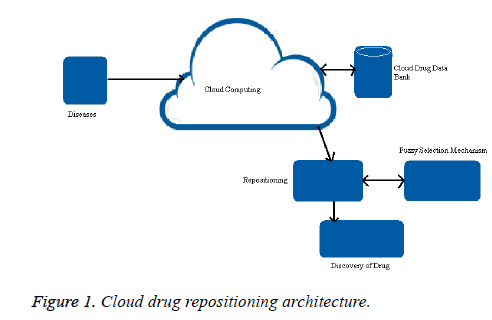
The design of drug repositioning approach by using cloud computing over conventional method is shown in Figure 1. This proposed method has four steps to discover a new drug. The four steps are namely input (disease), accessing cloud drug data bank, Repositioning which involves fuzzy repositioning selection mechanism and Drug discovery. The fuzzy repositioning selection mechanism is select methods for repositioning based on Fuzzy On-target drug repositioning and Fuzzy off-target drug repositioning. The drug compounds and molecular structure for each drug is unique and have complex processing methodology. When applying these processing methodologies in high computing environment there is a need of Knowledge Database consisting of information retrieved from the drugbank database needed for the processing. Sirota et al. combines the idea of signature based methodology to discover the relevance score of the drug and disease [4]. New uses for old drugs were identified numerously in various technologies [5-18].
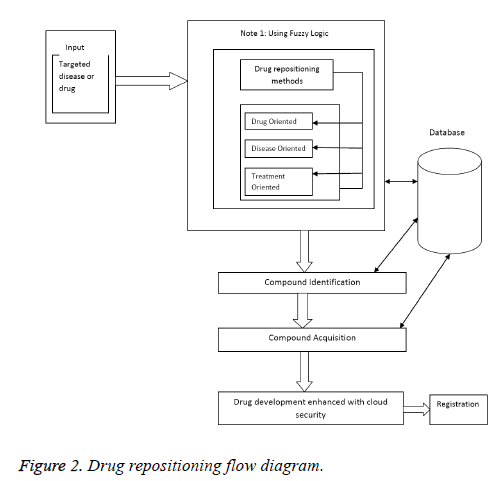
Figure 2 shows the workflow of the cloud based drug repositioning explained by first giving the targeted disease or drug as input to the system. Now the system identifies the drug repositioning methods (1. Drug oriented 2. Disease oriented 3. Treatment oriented) by acquiring knowledge from different sites online and that are stored under the cloud storage enable researchers to examine nearly all drug candidates and test on a relatively large number of diseases within significantly shortened time lines [5]. The virtual screening principle is sound, though, so we should examine its failings to date. There are three fundamental causes: 1. Impoverished data sources 2. The need for skilled practitioners 3. Simplistic, compromised modeling tools [19].
Available resources of cloud computing makes this possible by paying on demand (requirement) and Cloud computing not only provides required facilities for the computation and processing of big data but also serves as a service model. This method identification process is done by the fuzzy logic. The membership function of Fuzzy On-target drug repositioning and Fuzzy Off-target drug repositioning [20] is classified in to three variables namely low, medium and high. The PIPD controller is as risk threshold controller in Fuzzy risk assessment. The Fuzzy risk assessment set the threshold point. The PIPD controller gets the threshold point as an input and process for resource utilization. First it will check the error rate for the present (P) and past (I) error. Second it will check the error rate for the present (P) and feature (D) error. Then the sum of the risk threshold is given to the admission controller [1,2].
Enhanced Encryption Security Mechanism for Drug Databases
Security in cloud computing is provided broadly by the following services Virtualization, Federated Identity, Virtual Private Network and policy services [21-23]. The proliferation of online services makes the need for security to commercial data, demanding restricted access and privacy protection and critically important for cloud computing to reach its full potential. From the perspective of security, which has always been an important aspect of quality of service, Cloud Computing inevitably poses new challenging security threats for number of reasons.
In the proposed enhanced encryption standard the user image acts as a password to the database thus the access of database by trusted users is ensured. We compare the conventional text password and the proposed image password in terms of their CPU time, self-time and performance. The insights obtained through analysis shows the efficiency of the proposed method. We now use image as an example to discuss the problem formulation. The chosen image is encrypted with the primary key column of database. During database construction, the user encrypts the images using standard ciphers and protects.
The proposed cloud data security scheme uses Triple DES for encryption and Decryption of the image. Triple DES is a symmetric-key block cipher, which applies the Data Encryption Standard (DES) cipher algorithm three times to each data block.
Algorithm
Triple DES uses a "key bundle" that comprises three DES keys, K1, K2 and K3, each of 56 bits.
The encryption algorithm is:
ciphertext = EK3(DK2(EK1(plaintext)))
i.e., DES encrypt with K1, DES decrypt with K2, then DES encrypt with K3.
Decryption is the reverse:
plaintext = DK1(EK2(DK3(ciphertext)))
i.e., decrypt with K3, encrypt with K2, then decrypt with K1.
By using this proposed algorithm helps to store their confidential drug data securely through encryption in the untrusted cloud database.
Comparison between Conventional Text Password and Proposed Scheme
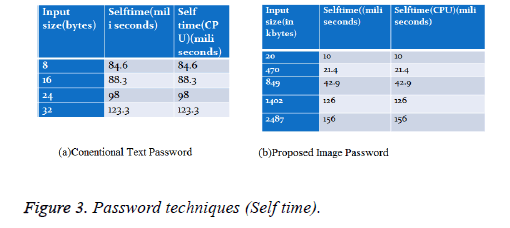
Comparative self-time (in milliseconds) of text password and image password techniques: A dataset of 1000 data is analyzed to compare the Self time of the proposed scheme and the conventional password. A good confidentiality-preserving secure database should retain high authentication accuracy as possible when compared to conventional text password.
From the results it is easy to observe that image password has an advantage over conventional password in terms of self-time as shown in Figure 3.
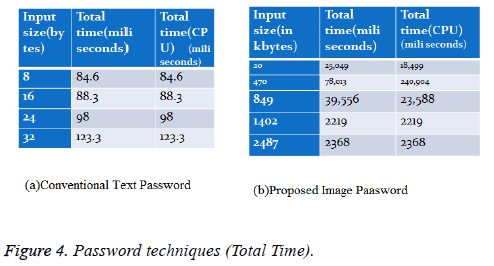
Comparative total time (in milliseconds) of text password and image password techniques: A dataset of 1000 data is analyzed to compare the Total time of the proposed scheme and the conventional password. A good confidentialitypreserving secure database should retain high authentication accuracy as possible when compared to conventional text password (Figure 4).
From the results it is easy to observe that image password takes a higher Total Time as compared to conventional text password.
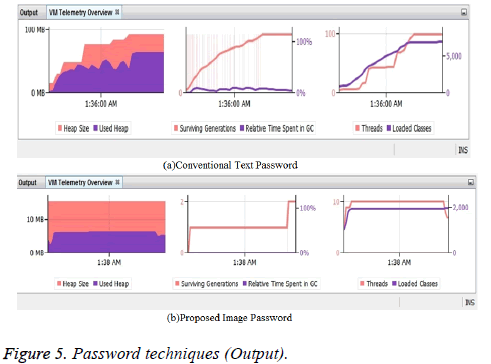
Comparative VM telemetric overview of text password and image password: A good confidentiality-preserving secure database should retain high authentication accuracy as possible when compared to conventional text password. From the results it is easy to observe that image password technique has lesser heap size as compared to conventional text password technique (Figure 5).
Advantages of Cloud Drug Repositioning over Classic Drug Discovery Process
Virtual screening fits the cloud computing model perfectly because it is so inherently parallel: you pay no extra for using 1,000 CPUs for one hour, rather than waiting 100 hours for 10 CPUs to do the same job.
Conclusion and Perspective
Cloud based drug repositioning offers good pace for discovery of new drug with significant utilization of cloud resources, smaller investment along with enhanced Image Secure Data Base-as-a Service (ImageSecureDBaaS) to secure drug databases. By comparing with conventional approach, the proposed cloud based approach gives more flexibility, computational efficiency, cost effectiveness and secure databases. Dynamic updation of knowledge database is challenging and necessary to avoid discovery of same drug by more than one person.
References
- Geetharamani G, Padma M, Kanimozhi P. Self Adapting System To Improve Resource Utilization In Virtual Machine Environment Under PIPD Controller. Int J Appl Eng Res 2015; 10: 3881-3885.
- Geetharamani G, Padma M. Survey and comparative study on strategic of provisioning in cloud computing environment. Australian J Basic Applied Sci 2014; 8: 344-352.
- Phelps K. Repositioning drugs to enhance a product’s lifecycle. Drug Disc Today Ther Strateg 2011; 8: 97–101.
- Sirota M. Discovery and preclinical validation of drug indications using compendia of public gene expression data. Sci Transl Med 2011.
- Jin G. Toward better drug repositioning: prioritizing and integrating existing methods into efficient pipelines. Drug Disc Today 2014.
- Agostino PV, Plano SA, Golombek DA. Sildenafil accelerates reentrainment of circadian rhythms after advancing light schedules. Proc Natl Acad Sci USA 2007; 104: 9834-9839.
- Tartaglia LA. Complementary new approaches enable repositioning of failed drug candidates. Expert Opin Invest Drugs 2006; 15: 1295-1298.
- Aronson JK. Old drugs - new uses. Brit J Clin Pharmacol 64: 563-565.
- Hughes B. 2007 FDA drug approvals: a year of flux. Nat Rev Drug Discov 2007; 7: 107–109.
- Ng SS, Brown M, Figg WD. Thalidomide, An antiangiogenic agent with clinical activity in cancer. Biomed Pharmacother 2002; 56: 194-199.
- Bernard P, Dufresne - Favetta C, Favetta P, Do QT, Himbert F, Zubrzycki S. Application of drug repositioning strategy to TOFI-SOPAM. Curr Med Chem 2008; 15: 3196.
- Bisson WH, Cheltsov AV, Bruey - Sedano N, Lin B, Chen J, Goldberger N. Discovery of antiandrogen activity of nonsteroidal scaffolds of marketed drugs. Proc Nat Acad Sci USA 2007; 104: 11927.
- Jarvis L. Teaching an old drug new tricks, Chem Eng News 2006; 84: 5.
- Campas C. Drug repositioning summit: Finding new routes to success. Drug News Perspect 2009; 22: 126.
- Ghofrani HA, Osterloh IH, Grimminger F. Sildenafil: From angina to erectile dysfunction to pulmonary hypertension and beyond. Nat Rev Drug Discov 2006; 5: 689-702.
- Padhy BM, Gupta YK. Drug repositioning: Re-investigating existing drugs for new therapeutic indications. J Postgrad Med 2011; 57: 153-160.
- Sirk K. Everything old is new again. Drug Disc News 2013.
- Fukuoka Y, Takei D, Ogawa H. A two-step drug repositioning method based on a protein-protein interaction network of genes shared by two diseases and the similarity of drugs. Bioinf 2013; 9: 89-93.
- Padma M, Geetharamani G,Pandian JA.New Therapeutic Applications for Drug Repositioning on the Cloud Computing.International Conference on Inter Disciplinary Research in Engineering and Technology, Delhi,India, 2015.
- Yang SJ, Lai PC, Lin J. Design Role-Based Multi-Tenancy Access Control Scheme for Cloud Services, 2013.
- Popa RA, Redfield CMS, Zeldovich N, Balakrishnan H. CryptDB: Protecting Confidentiality with Encrypted Query Processing, Proc. 23rd ACM Symp. Operating Systems Principles, 2011.
- Sakthivel K, Jayanthiladevi A , Kavitha C. Automatic detection of lung cancer nodules by employing intelligent fuzzy cmeans and support vector machine. Biomed Res 2016; 27: S123-S127.